How to use Acceptance Criteria to deliver high quality Product Features
Credits: Published by our strategic partner Kaiburr
As a Product Manager, when you define features for development and / or enhancement, it is important to ensure that the requirements are well-defined and unambiguous. This ensures that the product is built according to the vision and intent that you have for it.
Lack of rigorous, well-defined Acceptance Criteria can lead to delays and even poorly built products which do not answer the need for which they were intended.
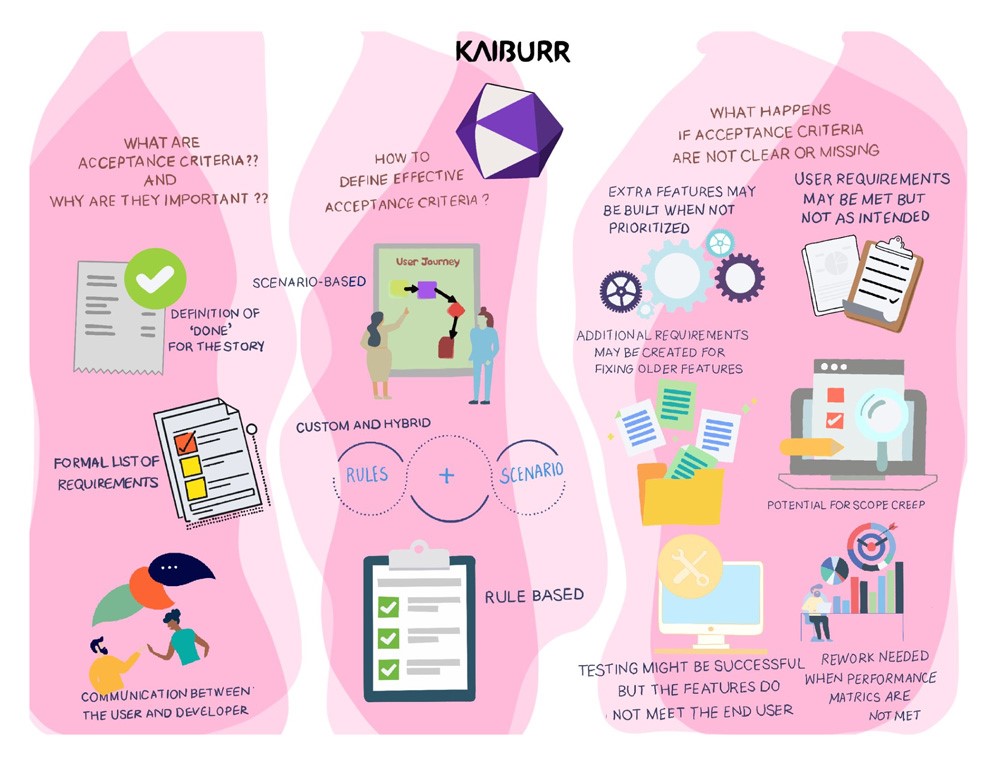
What are acceptance criteria and why are they important
- Acceptance criteria in a story are the definition of ‘done’ for the story.
- They are a formal list of requirements that describe a set of features, capabilities, conditions that meet the user’s needs as defined in the story.
- Acceptance criteria set the bounds for the story and the scope of the work the story entails.
- They are a key piece of communication between the user / client / product owner and the builder / developer.
- While they do not define the implementation details and ‘how’ the story must be built, the acceptance criteria define ‘what’ requirements must be met for the story to be considered ‘done’.
- This allows the development teams to design and build the user story with a clear idea of what must be built and what must be tested.
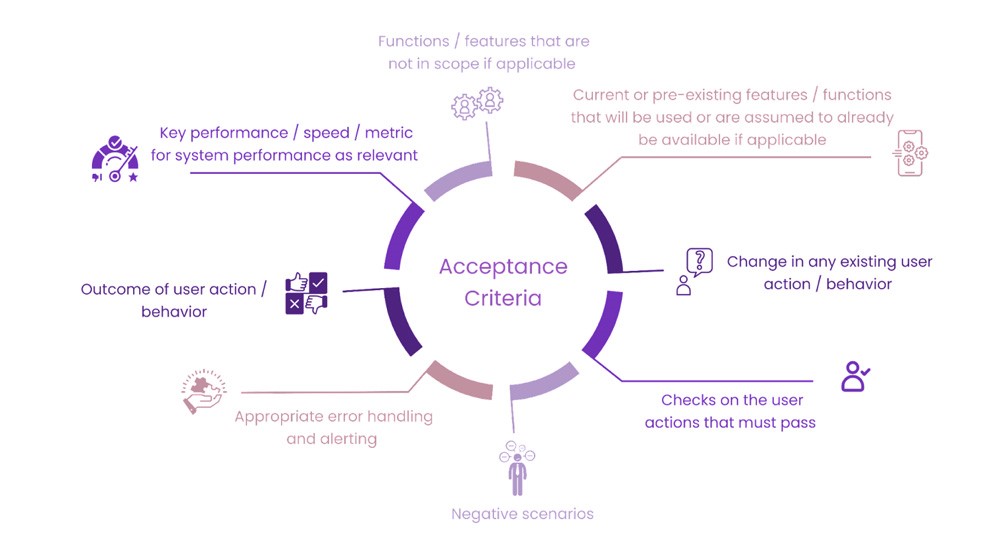
Acceptance criteria should define:
- current or pre-existing features / functions that will be used or are assumed to already be available if applicable
- change in any existing user action / behavior
- checks on the user actions that must pass
- negative scenarios
- appropriate error handling and alerting
- outcome of user action / behavior
- key performance / speed / metric for system performance as relevant
- functions / features that are not in scope if applicable
Who defines acceptance criteria:
Usually acceptance criteria are defined by consensus. Ideally the user behavior and system performance expectation, as perceived by a user, should be defined by the Product Manager. Additional standards that must be met for performance, tracking and internal system use may be defined by the Development and Operations teams as well.
What are effective acceptance criteria:
There are several ways to define acceptance criteria and depending upon the type of product and user story, different methods may be more relevant or easier to implement.
Before jumping into the actual methods that may be used to define acceptance criteria, the following points must be kept in mind:
- Anyone who reads the acceptance criteria should be able to understand them
- Must define ‘What’ must be done not ‘How’ it must be done
- Must always be from the user’s perspective
- Must be specific, clear, concise and testable
- Must be within the scope of the story
How to define effective acceptance criteria
- Scenario-based acceptance criteria define the user journey or user experience through describing various scenarios that the user will encounter and how the experience must be handled.
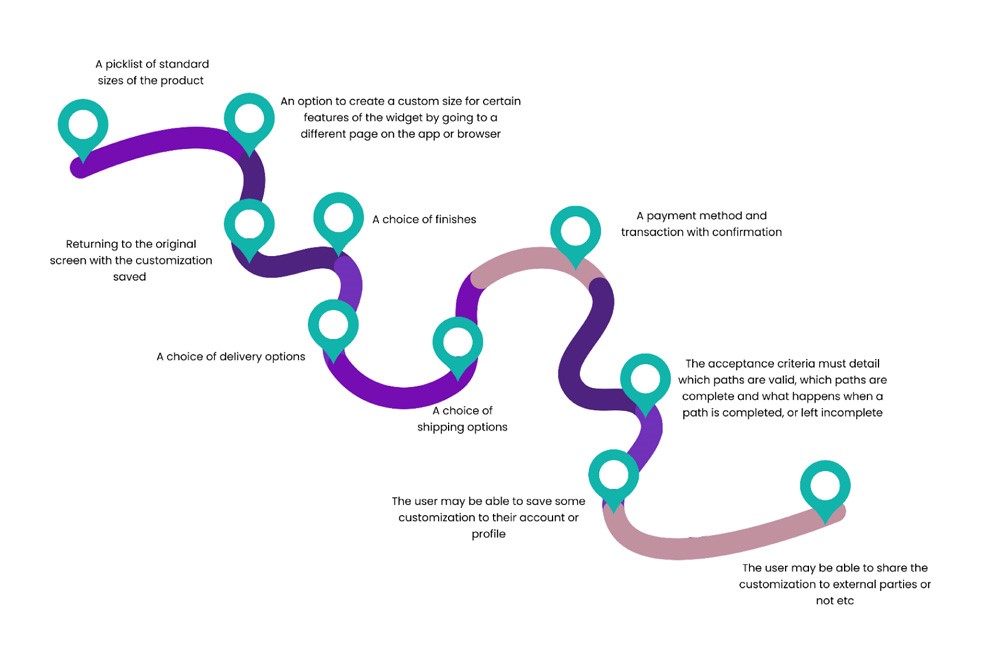
Example: A user has the choice of several options for choosing and customizing a widget that we build for them: The navigation paths that are possible and allowed should be detailed.
- A picklist of standard sizes of the product
- An option to create a custom size for certain features of the widget by going to a different page on the app or browser.
- Returning to the original screen with the customization saved.
- A choice of finishes.
- A choice of delivery options.
- A choice of shipping options.
- A payment method and transaction with confirmation.
- The acceptance criteria must detail which paths are valid, which paths are complete and what happens when a path is completed, or left incomplete.
- The user may be able to save some customization to their account or profile.
- The user may be able to share the customization to external parties or not etc.
- Rule based acceptance criteria usually list a set of criteria that must be met for the story to be ‘done’. These include display fields and branding colors / logos etc. , size, appearance and shapes of visual elements.
Example: A landing page for a first time or returning user, who is requested to create an account or login with existing account:
- The logos and standard branding colors for the page or app are displayed.
- Check for existing users with email or userid as the case may be.
- Checks for password requirements for strength.
- Checks for MFA rules.
- Checks for recovery options etc.
- Custom and hybrid Rules+Scenarios used together are, not surprisingly, the most common form of defining acceptance criteria for complex product features, where both Scenarios of user experience are defined along with specific Rules and additional testable descriptive requirements.
No one way of defining criteria is better than another, and the best way is usually the one that answers all questions that any reader of the story may have, be it from the product team, development team, executive sponsor or another product and project stakeholder.
What happens if acceptance criteria are not clear or missing:
Unclear acceptance criteria can cause many headaches and derailments in the product development process:
- User requirement may be met but not in the way intended by the product manager / or described in the product roadmap.
- Testing may be successfully completed but the feature does not meet the user’s needs.
- Rework may be needed or additional requirements may be created for fixing or changing older features affected by current change.
- Rework is needed as performance metrics are poor or not met.
- Error handling for negative scenarios is ambiguous or undefined.
- Extra features / functions may be built when not needed or prioritized.
- Potential for scope creep
- Additional spending of resources – time and money – to ‘fix’ the story
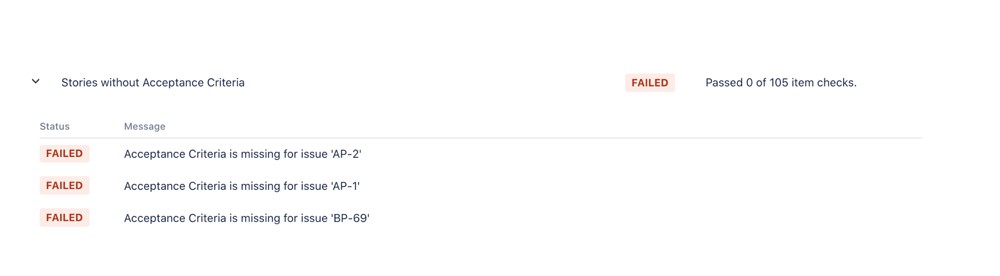
Kaiburr helps identify stories missing acceptance criteria like the example below –
With just 15 minutes of configuration, Kaiburr produces real time actionable insights on end-to-end software delivery with 350+ KPIs, 600+ best practices and AI/ML models. Kaiburr integrates with all the tools used by the enterprise Agile teams to collect the metadata and generates digital insights with a sophisticated next generation business rules engine.
Reach us at marketing@sifycorp.com to get started with metrics driven continuous improvement in your organization.
Credits: Published by our strategic partner Kaiburr
eLearning Solutions to Mitigate Unconscious Hiring Bias
The Hiring Bias
In study after study, the hiring process has been proven biased and unfair, with sexism, racism, ageism, and other inherently extraneous factors playing a malevolent role. Instead of skills or experience-based recruiting, it is often the case that interviewees get the nod for reasons that have little to do with the attributes they bring to an employer.
“This causes us to make decisions in favor of one person or group to the detriment of others,” says Francesca Gino, Harvard School of Business professor describing the consequences in the workplace. “This can stymie diversity, recruiting, promotion, and retention efforts.”
Companies that adhere to principles of impartial and non-biased behavior and that want to increase workforce diversity are already hard-pressed to hire the best talent in the nation’s current environment of full-employment and staff scarcity.
Five Main Grounds for Hiring Bias
Researchers have identified a dozen or so hiring biases, starting with a recruiting ad’s phrasing that emphasizes attributes such as “competitive” and “determined” that are associated with the male gender. In fact, study findings have reiterated that even seasoned HR recruiters often fall prey to faulty associations.
Here are five of the most frequently cited reasons for the unintended bias in the hiring process:
- Confirmation Bias: Instead of proceeding with all the traditional aspects of an interview, interviewers often make up their minds in the first few minutes of talking with a candidate. The rest of the interview is then conducted in a manner to simply confirm their initial impressions.
- Expectation Anchor: In this case, interviewers get fixated on one attribute that the interviewee possess at the expense of what backgrounds and skills other applicants can bring to the interview process.
- Availability Heuristic: Although this may sound somewhat technical, all it means is that the interviewer’s judgmental attitude takes over. Examples might be the applicant’s height or weight, or something as mundane as his or her name, reminding the interviewer of someone else.
- Intuition-Based Bias: This applies to interviewers who pass judgment based on their “gut feeling” or “sixth sense”. Instead of evaluating the candidate’s achievements, this depends solely on the interviewer’s frame of mind and his or her own prejudices.
- Confirmation Bias: When the interviewer has preconceptions on significant aspects of what an applicant ought to offer, everything else gets blotted out. This often occurs when, within the first few minutes of talking with an applicant, the interviewer decides in his or her favor at the expense of everything else that other candidates may have to offer.
Why Bias Is a Problem
In a book titled The Difference: How the Power of Diversity Creates Better groups, Firms, Schools and Societies, Scot E. Page, professor of Complex Systems, Political Science and Economies at the University of Michigan, employs scientific models and corporate backgrounds to demonstrate how diversity in staffing leads to organizational advantages.
Despite the mountain of evidence, the fact remains that many fast-growing companies are still not deliberate enough in their recruiting practices, often times ending up allowing unconscious biases to permeate in their methods.
Diversity in hiring, an oft-used term, is essentially a reflection on different ways of thinking rather than on other biases. For example, a group of think-alike employees might have gotten stuck on a problem that a more diverse team might have tackled successfully using diverse thinking angles.

Automated Solutions
Although hiring bias is normally shunned, this in no way implies that it doesn’t proliferate amidst large and small organizations alike. The tech industry—and Silicon Valley in particular—was shaken recently by accusations of bias in the workplace, driving many HR managers and C-Suite executives to look for “blind” hiring solutions.
To pave the way for a more diverse workforce—one that is built purely on merit—there is recruiting software built to systematize vetting and maintain each candidate’s anonymity. These packages enable companies to select candidates through a blind process. Instead of looking at an applicant’s resumé through the usual prism of schools, diplomas and past company employers, the first wave of screening can be done based purely on abilities and achievements.
Other packages also enable the employer to write blind recruiting ads, depicting job descriptions that do away with key phrases and words that are associated with a particular demographic—masculine-implied words such as “driven”, “adventurous”, or “independent”, and those that are feminine-coded such as “honest”, “loyal”, and “interpersonal”.
eLearning Case Studies
Companies are now attempting to make diversity and inclusion—from entry-level employees to the executive suite—hallmarks of their corporate culture. With an objective to identify and address unconscious bias in all processes and behaviors, companies can introduce unconscious bias training curriculum for first-line managers, by calling on eLearning companies for their eLearning courseware and content.

Confronting Hiring Bias in a Virtual Reality Environment
Virtual Reality (VR) technology can further boost unintended hiring bias. In a simulated setting, the user manipulates an avatar that was able to assume any number of demographics for applicants in the hiring process. Based on the gender or ethnicity of the avatar, the user experiences bias during question and answer sessions. The solution would use an immersive VR environment, a diverse collection of avatars, and sample scenarios to pinpoint to participants where bias is demonstrated and understood.
Transform High-tech Curriculum with Sify eLearning Experts
For high-tech curriculums, Training Directors (TD) need to address Millennial and Gen-Z (MGZ) workforce’s
need for self-paced content in addition to the traditional instructor-led, in-person courses. “Meeting the learner”
has become a term reflecting a corporate necessity. In a perfect world, SME’s could easily transform their
knowledge and the classroom instruction to engaging, effective self-paced content. Often, organizations do not
have the bandwidth to keep instructors out of the classrooms for long periods to support content creation.
To Infinity and Beyond!
Vamsi Nekkanti looks at the future of data centers – in space and underwater
Data centers can now be found on land all over the world, and more are being built all the time. Because a lot of land is already being utilized for them, Microsoft is creating waves in the business by performing trials of enclosed data centers in the water.
They have already submitted a patent application for an Artificial Reef Data Center, an underwater cloud with a cooling system that employs the ocean as a large heat exchanger and intrusion detection for submerged data centers. So, with the possibility of an underwater cloud becoming a reality, is space the next-or final-frontier?
As the cost of developing and launching satellites continues to fall, the next big thing is combining IT (Information Technology) principles with satellite operations to provide data center services into Earth orbit and beyond.
Until recently, satellite hardware and software were inextricably linked and purpose-built for a single purpose. With the emergence of commercial-off-the-shelf processors, open standards software, and standardized hardware, firms may reuse orbiting satellites for multiple activities by simply downloading new software and sharing a single spacecraft by hosting hardware for two or more users.
This “Space as a Service” idea may be used to run multi-tenant hardware in a micro-colocation model or to provide virtual server capacity for computing “above the clouds.” Several space firms are incorporating micro-data centers into their designs, allowing them to analyze satellite imaging data or monitor dispersed sensors for Internet of Things (IoT) applications.

HPE Spaceborne Computer-2 (a set of HPE Edgeline Converged EL4000 Edge and HPE ProLiant machines, each with an Nvidia T4 GPU to support AI workloads) is the first commercial edge computing and AI solution installed on the International Space Station in the first half of 2021 (Image credit: NASA)
Advantages of Space Data Centers
The data center will collect satellite data, including images, and analyze it locally. Only valuable data is transmitted down to Earth, decreasing transmission costs, and slowing the rate at which critical data is sent down.
The data center might be powered by free, abundant solar radiation and cooled by the chilly emptiness of space. Outside of a solar flare or a meteorite, there would be a minimal probability of a natural calamity taking down the data center. Spinning disc drives would benefit from the space environment. The lack of gravity allows the drives to spin more freely, while the extreme cold in space helps the servers to handle more data without overheating.
Separately, the European Space Agency is collaborating with Intel and Ubotica on the PhiSat-1, a CubeSat with AI (Artificial Intelligence) computing aboard. LyteLoop, a start-up, seeks to cover the sky with light-based data storage satellites.
NTT and SKY Perfect JV want to begin commercial services in 2025 and have identified three primary potential prospects for the technology.
The first, a “space sensing project,” would develop an integrated space and earth sensing platform that will collect data from IoT terminals deployed throughout the world and deliver a service utilizing the world’s first low earth orbit satellite MIMO (Multiple Input Multiple Output) technology.
The space data center will be powered by NTT’s photonics-electronics convergence technology, which decreases satellite power consumption and has a stronger capacity to resist the detrimental effects of radiation in space.
Finally, the JV is looking into “beyond 5G/6G” applications to potentially offer ultra-wide, super-fast mobile connection from space.

The Challenge of Space-Based Data Centers
Of course, there is one major obstacle when it comes to space-based data centers. Unlike undersea data centers, which might theoretically be elevated or made accessible to humans, data centers launched into space would have to be completely maintenance-free. That is a significant obstacle to overcome because sending out IT astronauts for repair or maintenance missions is neither feasible nor cost-effective! Furthermore, many firms like to know exactly where their data is housed and to be able to visit a physical site where they can see their servers in action.
While there are some obvious benefits in terms of speed, there are also concerns associated with pushing data and computing power into orbit. In 2018, Capitol Technology University published an analysis of many unique threats to satellite operations, including geomagnetic storms that cripple electronics, space dust that turns to hot plasma when it reaches the spacecraft, and collisions with other objects in a similar orbit.
The concept of space-based data centers is intriguing, but for the time being-and until many problems are worked out-data centers will continue to dot the terrain and the ocean floor.
Elite Teams recover Systems from Failures in No time (MTTR)
Credits: Published by our strategic partner Kaiburr
Effective Teams in a right environment under Transformative Leadership by and large achieves goals all the time, innovates consistently, resolves issues or fixes problems quickly.
DevOps is to primarily improve Software Engineering practices, Culture, Processes and build effective teams to better serve and delight the Users of IT systems. DevOps focuses on productivity by Continuous Integration and Continuous Deployment (CI-CD) to effectively deliver services with speed and improve Systems Reliability.
The productivity of a System is higher with high performance teams and slower with low performance teams. High performance teams are more agile and highly reliable. We can have better insights on Team performance by measuring Metrics.
DORA (DevOps research and assessment) with their research on several thousands of software professionals across wide geographic regions had come up with their findings that the Elite, High performance, medium and low performance can be differentiated by just the four metrics on Speed and Stability.
The metric ‘Mean time to restore(MTTR) ‘, is the average time to restore or recover the system to normalcy from any production failures. Improving on MTTR, Our teams become Elite and reduces the heavy cost of System downtime.

Measure MTTR
MTTR is the time measured from the moment the System fails to serve the Users or other Systems requests in the most expected way to the moment it is brought back to normalcy for the System’s intended response.
The failure of the System could be, because of semantic errors in the new features or new functions or Change requests deployed, memory or integration failures, malfunctioning of any physical components, network issues, External threats(hacks) or just the System Outage.
The failure of the running system against its intended purpose is always an unplanned incident and its restoration to normalcy in the least possible time depends on the team’s capability and its preparedness. Lower MTTR values are better and a higher MTTR value signifies an unstable system and also the team’s inability to diagnose the problem and provide a solution in less time.
MTTR doesn’t take into account the amount of time and resources the teams spend for their preparedness and the proactive measures but its lower value indirectly signifies teams strengths, efforts and Savings for the Organization. MTTR is a measure of team effectiveness.
As per CIO insights, 73% say System downtimes cost their Organization more than $10000/day and the top risks to System availability are Human error, Network failures, Software Bugs, Storage failures and Security threats (hacks).
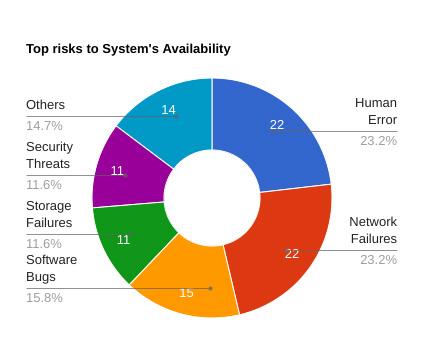
How to Calculate MTTR
We can use a simple formula to calculate MTTR.
MTTR, Mean time to restore = Total Systems downtime / total no. of Outages.
If the System is down for more time, MTTR is obviously high and it signifies the System might be newly deployed, complex, least understood or it is an unstable version. A system down for more time and more frequently causes Business disruptions and Users dissatisfaction. MTTR is affected by the team’s experience, skills and the tools they use. A highly experienced, right skilled team and the right tools they use helps in diagnosing the problem quickly and restoring it in less time. Low MTTR value signifies that the team is very effective in restoring the system quickly and that the team is highly motivated, collaborates well and is well led in a good cultured environment.
Well developed, elite teams are like the Ferrari F1 pit shop team, just in the blink of an eye with superb preparedness, great coordination and collaboration, they Change tyres, repairs the F1 Car and pushes it into the race. MTTR’s best analogy is the time measured from the moment the F1 Car comes into the pit shop till the moment it is released back onto the F1 track. All the productivity and Automation tools our DevOps teams use are like the tools the F1 pitstop team uses.

How to improve, lower MTTR
Going with the assumption that a System is stable and still the MTTR is considerably high then there is plenty of room for improvement. In the present times of AI, we have the right tools and DevOps practices to transform teams to high performance and Systems to lower MTTR. Reports of DORA says high performance teams are 96x faster with very low mean time to recover from downtime.
It seems they take very less time, just a few minutes to recover the System from failures than others who take several days. DevOps teams that had been using Automation tools had reduced their costs at least by 30% and lowered MTTR by 50%. The 2021 Devops report says 70% of IT organizations are stuck in the low to mid-level of DevOps evolution.
Kaiburr’s AllOps platform helps track and measure MTTR by connecting to tools like JIRA, ServiceNow, Azure Board, Rally. You can continuously improve your MTTR with near real time views like the following
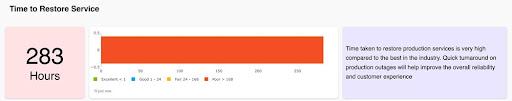
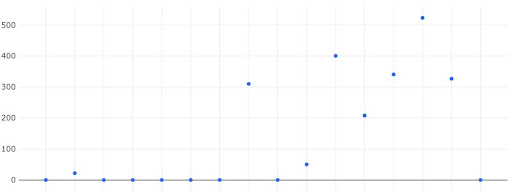
You can also track and measure other KPIs, KRIs and metrics like Change Failure Rate, Lead Time for Changes, Deployment Frequency. Kaiburr helps software teams to measure themselves on 350+ KPIs and 600+ Best Practices so they can continuously improve every day.
Reach us at marketing@sifycorp.com to get started with metrics driven continuous improvement in your organization.
Credits: Published by our strategic partner Kaiburr
Visit DevSecOps – Sify Technologies to get valuable insights
AI and human existence: The ABCs of ADLs
Explained: How even the simplest of day-to-day activities are deeply influenced by ML & AI. Will it become a life-changer?
On any given day, a regular human being does several activities which are performed ritually and without fail. From cleaning to eating and drinking and finding our way across our environments, human life involves many activities that are deemed Activity of Daily Living, or ADL. We have performed these activities in the past without any technological help or advice. Throughout human history, man has invented many a tool to improve the execution of these ADLs, and our current age is no different. Technologies such as ‘Machine Learning’ and ‘Artificial Intelligence’ have enabled many advancements to our lifestyle. Some assist us, however there a few that we need to be cautious about.
Let us stride through these ADLs one by one by following a simple activity timeline of a person’s one-day life as we discover how Machine Learning is shaping human life.
Morning – 5 AM to 10 AM
A day for us typically starts with several activities. Brushing, eating, washing, etc., are a few morning routines that we follow in our day-to-day life.
A day begins by waking up from sleep. Nowadays smart devices such as wrist-fit bands, and smartwatches tell us more about our sleep. These devices take leverage of AI and Machine Learning to provide accurate results with improvement. They help us to improve our sleep quality and behavior which in turn improves our health.

After waking up, we essentially brush our teeth to maintain hygiene and dental wellness. Even in this activity with the help of novel smart wrist devices and smart toothbrushes which use AI and Machine Learning, we study and measure our hand movements, direction, speed, etc., that improve the quality of our brushing which in turns keep our oral health in check. An example of such an application is Oral B Genius X.
Nowadays, washing our hands regularly to maintain hygiene and immunity is very important especially given the COVID scenario around the globe. Many kinds of research have been made to take advantage of the technological development to help in monitoring hand hygiene and give a quality assessment to an individual. Many privatized hospitals have tied up with several industries to implement a smart solution for providing hand hygiene quality assessment. The doctors from these hospitals take advantage of it daily to improve their hygiene and their patients’ as well. An example of such an application is The MedSense Clear system by the MIT Medlab Alumni.
Physical health and maintaining shape have become very underrated due to the new awareness around mental health and its importance. Nevertheless, staying in shape is a very important aspect of people’s lives as it indirectly constitutes mental well-being. Diet planning and eating healthy is something that must be taken care of. With the help of smart mobile and computer applications, we nowadays plan our diet efficiently. With the rise of ‘Machine Learning’, this system is scrutinized, and further research is being conducted to find solutions for problems such as people’s preferences in their eating habits to provide an even better solution.
Mid-Day Activities – 10 AM to 3 PM
Mid-day activities constitute a very wide range of tasks. We regularly use map applications to commute to a certain location. These applications use AI and Machine Learning extensively to provide the best route possible by predicting traffic and other obstacles well before we commute. These applications suggest the best means of transport and the best route to take, they even track and alert us on breakdown of transport services. Examples of such applications are Google Maps, Apple Maps, etc.
Many people work in closed environments either in the office or at home. We are always sedentary, and desk bound. It becomes inevitable to take breaks and go for a short walk and stretch ourselves. And, equally important is to keep ourselves hydrated. With the help of smart devices, we can track the amount of time that we sit continuously. They help us to take a break or even correct our posture if required. Some also help us stay hydrated and suggest improvements based on the environment and atmosphere quality around us. Examples of such devices are Apple Watch, Mi Band, etc.
Evening Activities – 3 PM to 8 PM
Evenings are when we generally try to relax after work and indulge in leisure activities that differs from individual to individual. These activities involve a lot of AI and Machine Learning as it takes advantage of our data right from our preferences to our recent practices. These technology-driven applications and systems need to be handled with utmost caution. We all use the e-commerce facility extensively as it helps us to reduce the time and energy to buy a product as it enables us to shop from wherever we are. This has huge benefits. But we sometimes are ignorant and innocent about the implications that might come. Few applications read our technology usage colossally as they keep track of us more than we know. They improve their recommendation system using this data with the help of AI and Machine Learning and suggest products well before we want to search. If we are not using an official or a recognized application, we are at risk of a privacy breach with the history of our shopping data being stolen or hacked.

Social media applications have invaded our lives. We connect via different platforms to share, exchange ideas and also to relax. However, some of these applications hold sensitive data about us. These applications have plenty of recommendation systems that are constantly updated to feed posts enjoyable to us. But are we compromising on the sensitive data like our name, address, phone number, etc., as well as our preferences that reveal who we are while doing so? An imminent danger to watch out for here is ‘data leakage’. Some of these applications never encode or cipher our passwords. Other activities during the evening include working out, which a few people prefer in the morning too. With the prevailing COVID situation, we have restricted using the gym frequently. Many applications and systems have been created to assist us to work from home. With the help of AI and Machine Learning, they streamline our workout routine.
End Day Activities – 8 PM to 5 AM
End-day activities help us unwind as we call it a day. We perform certain activities as mentioned previously like eating, brushing, washing, etc. Some smart devices assist us by providing an alarm to indicate our sleeping time. This heavily depends upon technology as it tracks our previous sleep history to let us know in what areas we need to improve. These applications help us learn from our sleep pattern, like how much time we spent in deep sleep and so on. This system heavily uses AI and other sensors to read our breathing, heartbeat and measures those accurately to provide insights. Many wristwatches and fit bands provide this feature.
As we get to the end of it, these applications help us save energy and time as well as lead an enriching life.Having said that, we must also be cautious regarding their influence on us. Take precautions and double-check the application for privacy policies. Always use trusted applications, instead of randomly selecting one that might store unwanted cookies to store sensitive data which might lead to an imminent threat. So, what’s your ADL?
In case you missed: