How IT Infrastructure Automation and Monitoring Can Revolutionise Your Nonprofit
IT Infrastructure Automation and Intelligent Monitoring; this is not a subject that most know too deeply about or may even recognise the level of importance it may have in any given organisation.
Scaling and Modernising IT for Nonprofits: Key Strategies for Success
Charitable organisations must keep up with technological advancements to remain effective and efficient. Modernising and scaling legacy IT infrastructure and web applications can seem daunting, but it’s essential for improving operations, enhancing security, and better serving your community.
Strategies and Tools to Improve Communication for Nonprofits
Effective communication is the backbone of any successful nonprofit organisation. Whether it’s engaging with staff, connecting with constituents, or building relationships with donors, clear and efficient communication can significantly enhance your organisation’s impact.
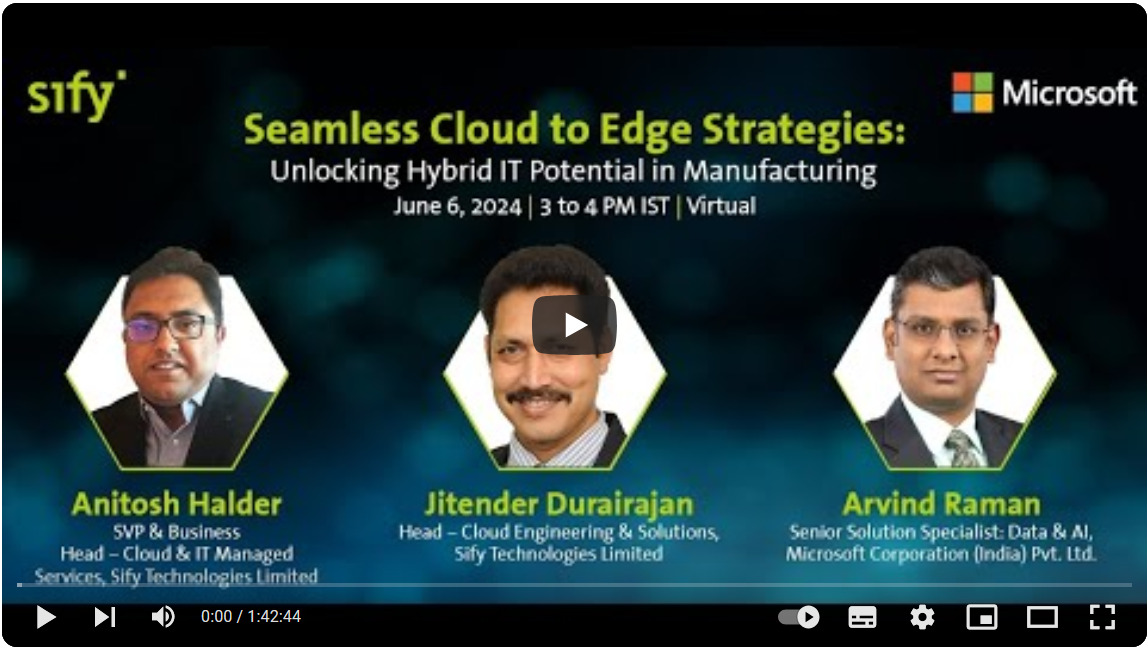
Seamless Cloud to Edge Strategies: Unlocking Hybrid IT Potential in Manufacturing
SPEAKERS:
Anitosh Halder, SVP & Business Head – Cloud & IT Managed Services, Sify Technologies
Jitender Durairajan, Head Cloud Engineering & Solutions, Sify Technologies
Arvind Raman, Senior Solution Specialist: Data & AI, Microsoft
V Ranganathan Iyer, Sr. EVP- IT, Group CIO, JBM Group
Kapil Mehrotra, Group CTO & CISO, Dhanuka Agritech
Kauser Khan, Vice President Information Technology, Maruti Suzuki India
DATE:
June 6, 2024 | 3:00 PM
DESCRIPTION:
To maximize the benefits of digital initiatives across all operational areas, organizations must go beyond modernizing their core to include the edge environment. For manufacturing companies looking to migrate their ERP to cloud platforms such as Azure, the transition demands robust integration between cloud and edge operations for real-time data processing and collection.
Service providers play a crucial role in assessing the current IT landscape to proposing the best suited hybrid/multi-cloud strategy to drive innovation into key operational areas like warehousing and logistics at the edge.
Organizations require integrated solutions encompassing connectivity, security, and managed services to ensure low latency, compliance, efficient data analytics, and to harness AI’s potential. This dual focus on cloud and edge modernization translates technological investments into tangible business outcomes and operational efficiencies, setting the stage for future innovations.
Modernize with SAP on GCP to Unleash Superior Customer Experience
SPEAKERS:
Anitosh Halder, SVP & Business Head – Cloud & IT Managed Services, Sify Technologies
Shivam Shrivastav, SAP Sales Specialist, Google Cloud
DATE:
February 22, 2024 | 3:00 – 4:00 PM
DESCRIPTION:
An insightful presentation on Sify’s SAP Migration, Infrastructure, and Managed Services capabilities, Sify’s expertise in SAP migration, robust infrastructure solutions, and managed services for seamless operations. The session includes a fireside chat on SAP market trends, innovations, and choosing the right partner for SAP migration. Gain valuable knowledge from industry leaders and learn how Sify can enhance your SAP journey.
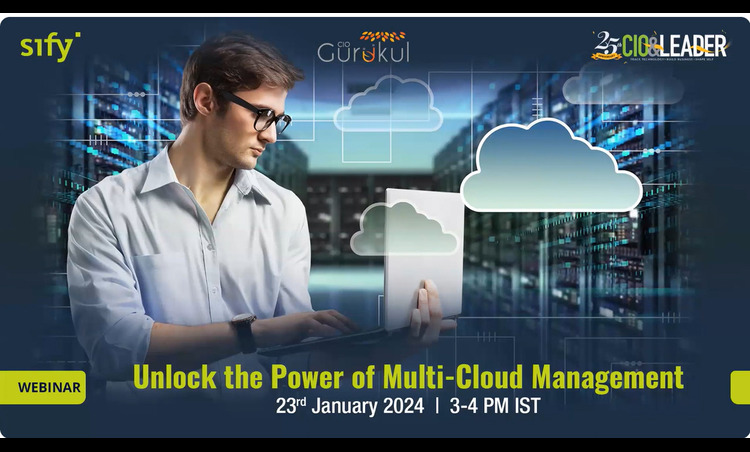
Unlock the Power of Multi-Cloud Management
SPEAKERS:
Anitosh Halder, SVP & Business Head – Cloud & IT Managed Services, Sify Technologies
Jitender Durairajan, Head Cloud Engineering & Solutions, Sify Technologies
Samik Mukherjee, Head IT – Infrastructure and Operations, LIC Housing Finance Limited
DATE:
January 23, 2024 | 3:00 PM
DESCRIPTION:
A presentation on Sify’s Hybrid/Multi-Cloud Management Capability along with key insights from our latest IDC-Sify Cloud Spotlight Paper. Followed by a riveting fireside chat delving into current market trends, challenges of cloud security and compliance in BFSI sector and the need for a robust cloud infrastructure in an organization.
Cyber Security for Nonprofits: Lessons from Past Cyber Attacks
Non-profit and charitable organisations are facing an increase in cyber security challenges. Often with limited resources and a wealth of sensitive data, nonprofits have become prime targets for cybercriminals.
Past Cyber Attacks
In October 2023 the British Library experienced a ransomware attack that resulted in shutting down its computer, phone and WiFi systems for almost a month. After the Library refused to pay the ransom hundreds of files were released onto the dark web. Now, almost a year on, the Library has revealed its plans for cyber resilience going forward.
The National Trust also fell victim to a ransomware attack that disrupted their operations. Thankfully no data was stolen but the attack caused significant operational challenges and highlighted the vulnerabilities in their cyber defences.
These incidents underscore the importance of maintaining continual robust practices in cyber security for charities. Regular training, strong passwords, multi-factor authentication, and regular software updates can all help support this effort and mitigate the risks.
Common Entry Points for Cyber Attacks
By taking proactive steps, nonprofits can easily protect their valuable data and maintain the trust of their supporters. Attacks are not always that sophisticated. Attackers will often exploit several common entry points in charity systems that can easily be addressed.
Some of the most frequently used are Phishing Emails – which are deceptive emails designed to trick recipients into revealing sensitive information or downloading malicious software. They often appear to come from trusted sources.
Weak Passwords are still a common problem with simple or reused passwords making it easier for attackers to gain unauthorised access to accounts and systems.
Unpatched Software where outdated software may present vulnerabilities is another issue that attackers exploit. Regular updates and patches are crucial to close these security gaps.
By addressing these vulnerabilities through comprehensive security policies, regular training, and robust technical measures, charities can significantly reduce their risk of cyber-attacks.
Cybersecurity Success Stories
Some of the more successful breach prevention strategies that have been effectively implemented by various organisations, including charities are:
- Regular Security Training: One charity implemented quarterly cyber security training sessions for all staff and volunteers. This training included recognising phishing attempts, safe internet practices, and proper data handling procedures. As a result, they saw a significant decrease in successful phishing attacks.
- Multi-Factor Authentication (MFA): A non-profit organisation adopted MFA for all their online accounts and systems. This added layer of security required users to provide two or more verification factors to gain access, drastically reducing unauthorised access incidents.
- Regular Software Updates and Patching: Another charity established a strict policy for regular software updates and patching. By ensuring all systems and applications were up to date, they minimised vulnerabilities that could be exploited by attackers.
- Data Encryption: A large non-profit encrypts all sensitive data, both in transit and at rest. This meant that even if data was intercepted or accessed without authorisation, it would be unreadable without the proper decryption keys.
- Incident Response Plan: One organisation developed a comprehensive incident response plan, including regular drills and updates. This plan ensured that in the event of a breach, they could quickly contain and mitigate the impact, reducing downtime and data loss.
- Third-Party Vendor Assessments: A charity conducted thorough security assessments of all third-party vendors before engaging with them. This included reviewing their security policies, practices, and past incidents to ensure they met the charity’s security standards.
Implementing these strategies can significantly enhance an organisation’s cyber security posture and help prevent breaches.
Want to find out more about how best prepared your organisation is against cyber-attacks and where your vulnerabilities are?
Sify becomes First in India to Achieve NVIDIA DGX-Ready Data Center Certification for Liquid Cooling to Enable Breakthrough AI Performance
Chennai, India, September 02, 2024: Sify Technologies Limited (NASDAQ: SIFY), India’s leading Digital ICT solutions provider with global service capabilities spanning data center, cloud, networks, security and digital services, today announced it has become an NVIDIA colocation partner with the NVIDIA DGX-Ready Data Center
program, certified for liquid cooling.
The certification represents Sify’s data center deployment solution specifications to support 130 KW/rack capacity. The cooling solution also complies with ASHRAE’s 30 years ambient temperature guidelines.
NVIDIA DGX is a purpose-built platform for enterprise AI, powering AI workloads spanning analytics, training, and inference. It offers advanced compute density, performance and scale with a single, unified system that can power the complete enterprise AI lifecycle.
With the NVIDIA DGX platform and its supporting infrastructure technology ecosystem, Sify customers now have access to high-density supercomputing and powerful performance, offered in scalable and flexible AI infrastructure solutions and accessed through an extensive colocation footprint.
Speaking on the significant certification, Sharad Agarwal, CEO, Sify Infinit Spaces Limited, the data center subsidiary of Sify Technologies Limited, said “Sify’s data center business offers industry-grade cooling solutions. As AI/ML evolves across industries, Sify will be able to offer complete NVIDIA DGX-powered colocation along with NVIDIA’s advanced enterprise AI and data science software out of our MumbaiRabale campus and the upcoming premises of Noida and Chennai-Siruseri. We continue to invest in capacity across all our AI-ready data centers which are purposebuilt to support this emerging ecosystem in the data center industry.”
“AI is emerging as the competitive differentiator for businesses, and many organizations are looking for a colocation partner who can speed time to market, with the ability to securely host and scale AI infrastructure,” said Tony Paikeday, senior director, DGX platform, NVIDIA. “As India’s first NVIDIA DGX-Ready Data Center partner certified for liquid cooling, Sify offers enterprises a cost-effective solution that helps meet enterprise AI infrastructure requirements.”
About Sify Technologies
A Fortune India 500 company, Sify Technologies is India’s most comprehensive ICT service & solution provider. With Cloud at the core of our solutions portfolio, Sify is focussed on the changing ICT requirements of the emerging Digital economy and the resultant demands from large, mid and smallsized businesses.
Sify’s infrastructure comprising state-of-the-art Data Centers, the largest MPLS network, partnership with global technology majors and deep expertise in business transformation solutions modelled on the cloud, make it the first choice of start-ups, SMEs and even large Enterprises on the verge of a revamp.
More than 10000 businesses across multiple verticals have taken advantage of our unassailable trinity of Data Centers, Networks and Digital services and conduct their business seamlessly from more than 1600 cities in India. Internationally, Sify has presence across North America, the United Kingdom and Singapore.
Sify, www.sify.com, Sify Technologies and www.sifytechnologies.com are registered trademarks of Sify Technologies Limited.
Forward Looking Statements
This press release contains forward-looking statements within the meaning of Section 27A of the Securities Act of 1933, as amended, and Section 21E of the Securities Exchange Act of 1934, as amended. The forward-looking statements contained herein are subject to risks and uncertainties that could cause actual results to differ materially from those reflected in the forward-looking statements. Sify undertakes no duty to update any forward-looking statements.
For a discussion of the risks associated with Sify’s business, please see the discussion under the caption “Risk Factors” in the company’s Annual Report on Form 20-F for the year ended March 31, 2024, which has been filed with the United States Securities and Exchange Commission and is available by accessing the database maintained by the SEC at www.sec.gov, and Sify’s other reports filed with the SEC.
For further information, please contact:
Sify Technologies Limited
Mr. Praveen Krishna
Investor Relations & Public Relations
+91 9840926523
praveen.krishna@sifycorp.com
20:20 Media
Nikhila Kesavan
+91 9840124036
nikhila.kesavan@2020msl.com
Weber Shandwick
Lucia Domville
+1-212 546-8260
LDomville@webershandwick.com