Table of contents
Cloud security has entered a new era.The old perimeter-based models that once protected data centers are no longer enough.
In today’s hybrid and multi-cloud world, workloads scale in seconds, data moves across borders, and both defenders and attackers now wield artificial intelligence (AI).
Cloud security must evolve from being a layer to being part of the architecture itself — integrated, automated, and intelligent.
Importance of Cloud Security
Cloud environments are no longer static. They are elastic, distributed, and intelligent — powered by AI models that can auto-scale infrastructure and make orchestration decisions in real time.
Yet, this agility creates unprecedented exposure.
Misconfigurations, fragmented visibility, and identity sprawl multiply risk at machine speed. Attackers, too, are evolving — using AI to automate reconnaissance, craft polymorphic malware, and exploit supply chains faster than traditional defenses can respond.
The result is a security gap that can’t be closed by more tools — it requires rethinking cloud security from the ground up.
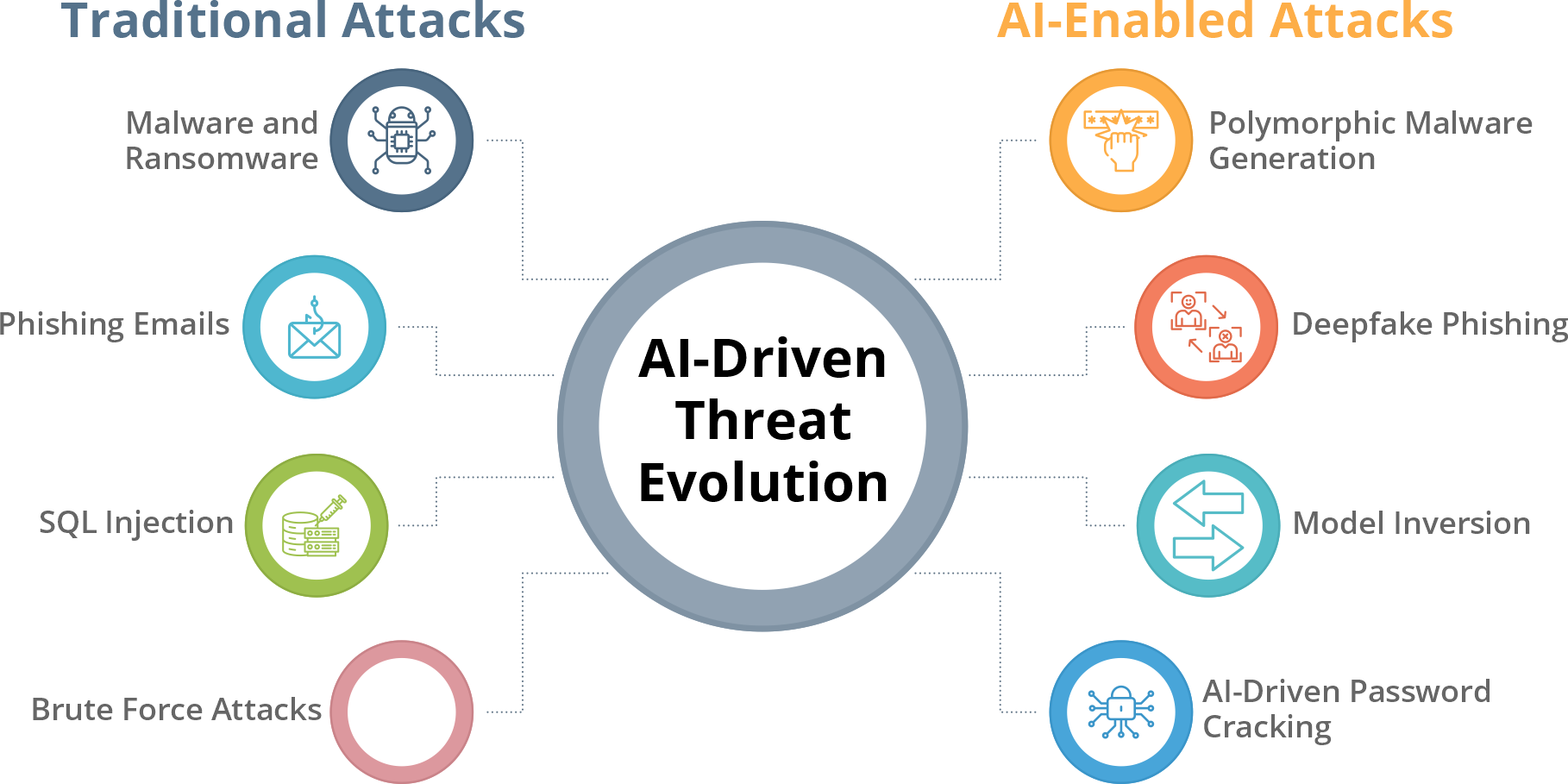
Top Challenges of Cloud Security in the AI Era
Cloud infrastructures have transformed, but many enterprises still secure them using outdated frameworks.
Here are the five critical cloud security challenges that most organizations underestimate — and why they’re growing more complex in the AI-driven landscape.
-
Lack of Cloud Visibility and Control
Visibility is the cornerstone of cloud security. Yet, in modern hybrid and multi-cloud environments, data is scattered across providers, APIs, and ephemeral workloads. Logs and telemetry exist in silos, while workloads may disappear before analysts can trace them.
This lack of unified visibility prevents teams from detecting misconfigurations or anomalous behavior early enough.
Modern Approach:
Security must be designed into the cloud fabric.Using tools like OpenTelemetry, cloud-native APIs, and CNAPP (Cloud-Native Application Protection Platforms), enterprises can achieve continuous, real-time observability across infrastructure, identity, and workloads. -
Cloud Velocity Outpacing Security Readiness
Cloud infrastructure operates at machine speed; human-driven security processes cannot keep up. Auto-scaling, ephemeral containers, and AI-orchestrated workloads change faster than static rule sets or manual approvals can respond.
Modern Approach:
Embed policy-as-code directly into CI/CD pipelines so that security becomes part of deployment, not an afterthought. Use automation frameworks like OPA (Open Policy Agent) and Kyverno to enforce continuous compliance.
Security must move with the cloud, not chase it. -
Signal-to-Noise Overload in Cloud Monitoring
Cloud environments generate millions of events per second — logs, alerts, telemetry, and runtime data. But volume doesn’t mean clarity. Many SOCs are overwhelmed by alert noise, missing the subtle signals that indicate sophisticated breaches or insider threats.
Modern Approach:
Adopt AI-assisted detection and correlation engines that analyze behavioral patterns, prioritize high-impact alerts, and map incidents to frameworks like MITRE ATT&CK for Cloud.
AI helps filter the noise, elevating signal quality and reducing analyst fatigue. -
Identity and Access Management Challenges in Cloud Security
Identity has become the new cloud perimeter. Every user, service account, and machine identity introduces potential vulnerabilities. Over-permissioned roles, abandoned tokens, and federated identities create lateral attack paths that bypass traditional network controls.
Modern Approach:
Shift to Zero-Trust Identity Models and Cloud Infrastructure Entitlement Management (CIEM). Implement Just-in-Time (JIT) and Just-Enough-Access (JEA) privileges, continuously monitored and enforced via policy-as-code.
Identity telemetry should be treated as core security data, not secondary logs -
Supply Chain Vulnerabilities in Cloud Ecosystems
The modern enterprise cloud is deeply dependent on open-source components, CI/CD pipelines, SaaS integrations, and third-party APIs. A single compromised dependency or poisoned software library can trigger cascading failures across production environments.
Modern Approach:
Adopt Software Bills of Materials (SBOMs) and SLSA frameworks to validate every component in your supply chain. Enforce runtime attestation and apply Zero Trust boundaries to minimize blast radius.Security is no longer about trusting vendors — it’s about verifying everything.
Why Ignoring Cloud Security Challenges Is Dangerous
Neglecting cloud security issues doesn’t just invite breaches — it undermines business continuity. AI-empowered attackers can weaponize stolen enterprise data to train malicious models, clone algorithms, or corrupt datasets.
Consequences include:
- Model manipulation and data poisoning
- Regulatory non-compliance and fines
- Erosion of customer trust
- Disruption of critical business services
How to Overcome Cloud Security Challenges in Modern Enterprises
As AI reshapes the threat landscape, enterprises must evolve from reactive defense to predictive resilience. That means embedding intelligence, automation, and governance into every layer of the cloud lifecycle.
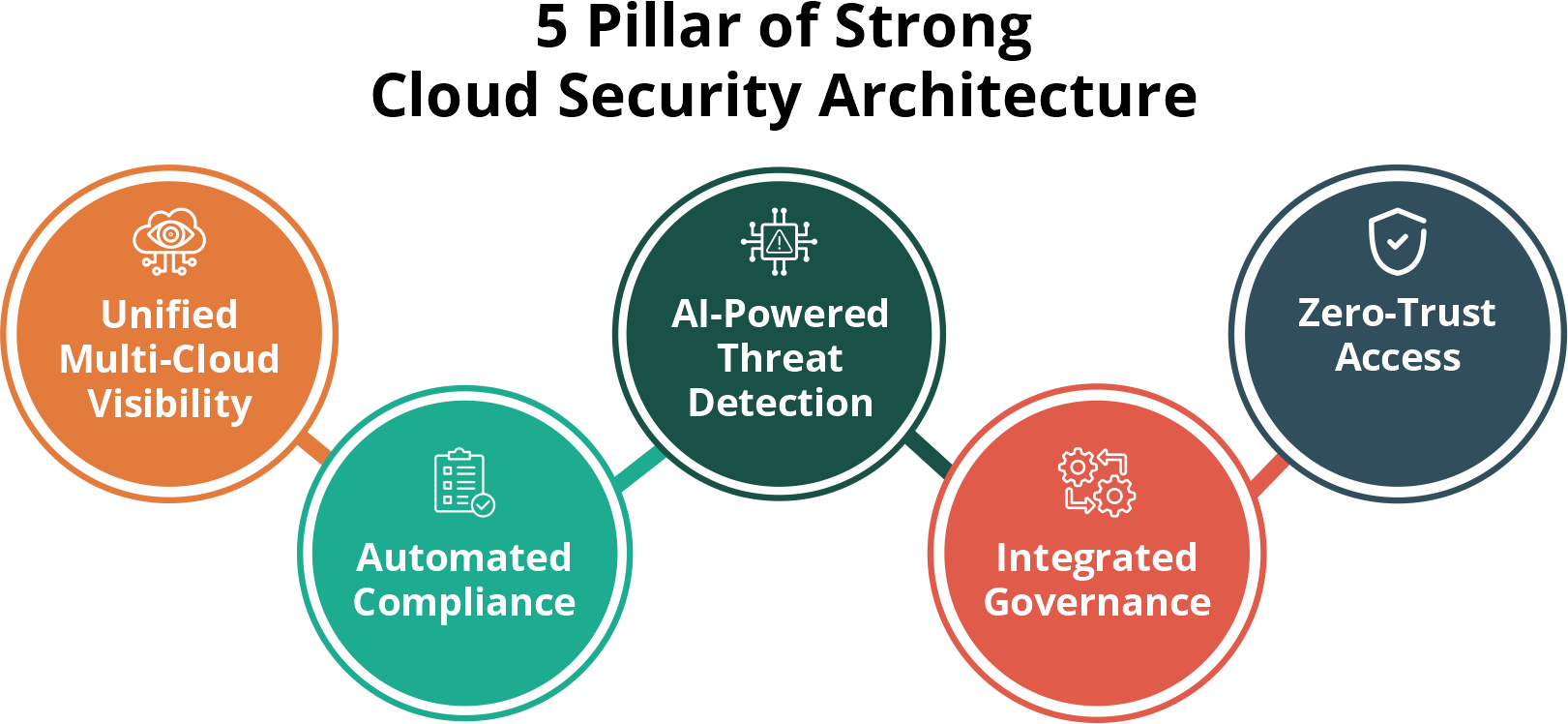
Pillars of a Strong Cloud Security Architecture
A truly resilient cloud security framework isn’t defined by how many tools an enterprise deploys — it’s defined by how well those tools, policies, and insights work together as an integrated ecosystem.
Modern security must be architectural, intelligent, and automated, built on five foundational pillars that enable continuous protection across hybrid cloud and multi-cloud environments.
-
Unified Multi-Cloud Visibility
You can’t protect what you can’t see. In a typical enterprise, workloads are spread across AWS, Azure, Google Cloud, and private clouds, each with its own visibility and control mechanisms.
This fragmentation creates blind spots — especially for ephemeral workloads, unmanaged APIs, and third-party integrations.Unified visibility solves this by converging telemetry from all environments into a single observability layer. Modern CNAPP platforms, OpenTelemetry streams, and cloud-native APIs integrate posture management, workload activity, and identity telemetry — giving enterprises a real-time, 360° view of their entire cloud landscape.
-
AI-Powered Threat Detection
The threat landscape has evolved from static signatures to adaptive, AI-enhanced attacks that morph faster than traditional rules can catch.
Enterprises now need defensive intelligence that can learn and evolve at the same pace. AI-powered analytics transform threat detection by analyzing behavior instead of patterns.Machine learning models can baseline normal activity across networks, containers, APIs, and identities — then flag deviations in real time.This reduces false positives and detects unknown or emerging threats that traditional systems miss.
With AI-based anomaly detection and predictive intelligence, organizations move from reactive incident response to proactive risk anticipation.
-
Automated Compliance and Governance
Cloud compliance is no longer a quarterly checklist — it’s a continuous process.
As data flows across regions and regulatory boundaries, enterprises must ensure that every workload, identity, and storage layer adheres to frameworks like GDPR, HIPAA, ISO 27001, and India’s DPDP Act. Automated compliance solutions continuously monitor configurations, access policies, and audit trails against these standards.
They detect drifts in real time and even remediate violations automatically.By integrating compliance checks directly into CI/CD pipelines, enterprises transform compliance from a reactive audit activity into a real-time assurance mechanism.
This not only reduces risk but also accelerates audit readiness — critical for industries like finance, healthcare, and government. -
Zero-Trust Access Architecture
In modern cloud ecosystems, the perimeter has dissolved — identity is the new control plane. Zero-Trust Architecture (ZTA) enforces the principle of “never trust, always verify”, ensuring that no user, device, or service gains access without continuous validation.
This model involves:
- Multi-Factor Authentication (MFA) and adaptive access controls
- Micro-segmentation of workloads to limit lateral movement
- Continuous monitoring of session behavior using AI-based identity analytics
Every connection is authenticated, authorized, and encrypted — whether it originates from a developer, an IoT endpoint, or an AI inference API.
For enterprises, Zero Trust is no longer optional; it’s the foundation for securing distributed and dynamic environments. -
Integrated Governance and Policy Enforcement
Cloud governance is what ensures security at scale.
When policies are defined manually or inconsistently across platforms, even small deviations can snowball into compliance violations or data exposure.Integrated governance unifies policy creation, enforcement, and validation across environments.
Using frameworks like policy-as-code, enterprises can encode their governance rules into machine-readable formats that are automatically applied during infrastructure provisioning and updates.This creates a closed-loop system — where policies aren’t just written but enforced by default across all clouds, workloads, and users.The result is a cloud environment that’s not only secure but predictably compliant and operationally efficient.
Sify Technologies: Enabling Intelligent and Integrated Cloud Security
Modern cloud security isn’t about adding more tools — it’s about creating architectural cohesion and AI-driven observability.This is where Sify Technologies leads.
Sify helps enterprises build resilience by design through its AI-powered managed security services, enabling continuous visibility, adaptive threat intelligence, and compliance automation.
Sify’s AI-Driven Cloud Security Capabilities:
- AI-Based Anomaly Detection: Detects and isolates irregular activity across workloads and control planes.
- Predictive Threat Intelligence: Identifies probable attack surfaces before they’re exploited.
- Automated Incident Response: Orchestrates immediate countermeasures to contain threats.
- Integrated Compliance Dashboards: Monitors regulatory adherence across hybrid and multi-cloud ecosystems.
- Zero-Trust Governance: Embeds identity verification and access control across every layer.
By unifying AI analytics, human expertise, and multi-cloud observability, Sify helps organizations transform security from a reactive burden into a strategic enabler.
The Future of Cloud Security: Building for an AI-First World
Cloud ecosystems will only grow more autonomous, elastic, and intelligent.
The challenge is not keeping up — it’s staying ahead.
The future of cloud security lies in:
- Architecture-driven defenses, not afterthought integrations
- Continuous verification, not static trust
- AI-assisted governance, not manual oversight
- Predictive protection, not reactive patching
Enterprises that embrace these principles will lead with speed and confidence — securing their data, models, and customers in real time.
Cloud security isn’t an endpoint — it’s a living, adaptive process.As AI becomes integral to both innovation and threat, enterprises must rethink their cloud foundations and redesign their defense strategies.
Sify Technologies empowers businesses to reinforce security at every layer, combining AI-powered automation with architectural intelligence to ensure that security moves at the speed of the cloud.
Ready to strengthen your cloud security foundation? Discover how Sify Technologies can help your enterprise achieve intelligent, architecture-led resilience. Speak to our experts today!
















































